Visit www.summermadness.co.uk for further information about the Festival
Cha'alt: Fuchsia Malaise
Yesssss! It's out. GET IT HERE.
This isn't the tippy-top final version, mind you. But it's farther along than a beta. The bookmarks, hyperlinks, and index is coming soon. Also, I'll be spotting and fixing typos over the next couple weeks.
What's in it? So much, dude. So much. 225 pages of the awesomeness you've gotten to know from Cha'alt. Some of that page count is previously released PDFs, such as OSR Like A Fucking Boss. That'll be in the fancy hardcover edition coming out this fall, so I wanted to include it in the PDF, as well. Everything in one place for convenience.
It took me almost a year to create Cha'alt: Fuchsia Malaise. It's jam-packed with gameable content. Some stuff you're probably expecting... the rest out of left-field.
I'm hoping to get some promotional boost from DriveThru, that's why it's ridiculously priced at $5. If you'd like to help out, blog about it, mention it on social media, or maybe write a review.
Thanks,
VS
Troops On Parade - 28Mm ECW Royalist
There is something very cathartic above setting a gaming collection out on the table for inspection. It's something I have reet enjoyed since starting this feature a few years back. Is it the joy of seeing the collection all together on the table or looking at the mass ranks with a sense of achievement, I don't know, but I do know that most of my fellow gamers will "get it".
As is becoming the norm at YG I have done a Yarkshire TV special on the Utubes to accompany the post (link above), for those that prefer static photos and text see below. For rules we play a homebrew modified version of Forlorn Hope.
All the figures are metal, this was before the days of cheap plastic soldiers, all the bases have a reassuringly weighty feel.
Starting on the right of the Army we have Prince Rupert (with his dog) and his group of Cavalry. These figures are all from Perrys bar the command which are Bicorne.
Over on the left I have my other wing of Cavalry, these are made up of Bicorne miniatures with a single unit of Renegade horse. At the head of the line is the Kings Mounted Lifeguard.
 |
| Another view of the left wing of Cavalry |
Those of you familiar with the period will recognise the flags of the units on show, rather than go for a specific army in terms of location and year I have picked and chosen from a number, with units from the Oxford Army and the Armies in Cheshire most prominent. Front rank here right to left as viewed are Talbots, Lifeguard and Ruperts.
The Lifeguard was a particular joy with the extra flags. Forlorn Hope is a 33:1 scale (in terms of men to models) game so my units are between 16 and 30 figures strong but generally 20 or 24. We have found that units are just not viable with less than 16 figures.
You can see from the bases that this is pre grass tufts days, some units in the Army have the original versions of tufts. We used to buy packs of coloured bristles from Railway Modelling shops, clump them up and glue one end, wait for them to dry and chop the top off. It was very slow and I have up on it, maybe 4 or 5 units in the Army have them.
My favourite unit in the Army is this little 16 figure Chester Milita Regiment with its own made up flag "Forward for God and Cheshire" it implores.
The personality figures are all Bicorne, here we have Sir Jacob Astley Commander of Foote.
Prince Rupert of the Rhine, Commander of Horse.
The main man himself King Charles, with Royal Standard carried by Sir Edmund Verney, odd figure, whatever I do the flag won't come off 🤔
The guns are mostly Old Glory with a couple of Perrys Figures, I do seem to have bought rather a lot.
In between the guns are a number of individually based figures from Wargames Foundry which cover a number of functions, Forlorn Hope, Engineers, Rappers and Snipers.
I love an army with lots of flags, it's not quite the Italian Wars but it's not far off. Most annoyingly after packing all the figs away I realised I forgot to put out my two units of Dragoons (mounted and dismounted) as well as my single unit of Cuirass 😣
Hopefully you have enjoyed that bit of fun, hopefully in a few weeks tine we will be back gaming.
Birth By S.T. Gulik, Book Review

Max lives in a world where the absurd is an everyday occurrence. It is a matter of how he reacts to the events affect his life, and his likelihood to stay alive. Max's world isn't much different from ours; it is only a matter of time from our now and his then.
Chakra Kong Part 1: Birth, or The Exquisite Sound of One Hand Falling Off a Turnip Truck (2nd edition) by S.T. Gulik is a look at our future through the lens of the absurd. I was given an advanced review copy by the author for review purposes.
Plot
In the future, the world progresses down the path of becoming stranger, odder, and more absurd. The division of society is greater. The threat of crime is greater. The threat of living is greater. The world has zombies living side by side with people who have been mutated by the acts of man and the acts of God. There are intelligent mutants living in the sewers (Iiites). People forced out of regular society because they look different and are stronger. And, there are the Riot Nrrds who are battling the Iiites with their intelligence and advanced degrees. Because they have come to understand, the Iiites are in more control of the world than normal people understand and want to care about.
In the middle of the chaos is Max, one of the masses who doesn't want to know and doesn't care. He is a guy who just wants to live his life by making enough money, having enough to drink, get high, and have sex. Unfortunately, for Max, he keeps getting thrust into the middle of the war between the Iiites and the Riot Nrrds.
Max is given the choice, at different times from both sides, to work for a particular side or die. He decides it is better to live another day. The middle is where he ends up, again and again, as he strives to keep himself in a place of relative safety. But he learns more about what his life is about.
Max has a destiny. He learns about his destiny from his spirit llama, by help from the mystics, who were introduced to by Jengists, who Max was directed to by the Night Noodles. With this greater knowledge, Max brings the first part of the war against the Iiite military arm to an end. Then with his arm wrapped around his Iiite girlfriend, he walks off to prepare for the next phase of the war after they get reacquainted.
Style
S.T. Gulik likes to write absurd stories. Birthis a prime example. Max's story happens in the future with many references to our current time and our past to anchor his absurd world with the absurd happenings people deal with today. Gulik just dials everything up a few notches to take it over-the-top.
Because of the extreme difference of our future society, Gulik starts out his book with some description of our future times. He gives the structure of society and some history of what is to come before we meet Max. At the end of the book, additional entries are available to reference and read more about a number of the elements he introduces.
Max for most of the story is a reactionary character. He would rather just be allowed to go home and live his life by getting drunk and high, but his destiny has other plans for him. Time and again he finds himself in a position where his decisions are limited to a point of basically having no option if he wants to continue living. Life and events are thrust upon him. This brings a number of other characters into Max's life he would not have met otherwise.
Most of the story is told through Max's perspective; however, readers are given insights to events by other characters. All of these combine together to show just how the world is out of control and rising to greater levels of absurdity.
Overall
You're never quite sure what to expect with the start of each chapter. Max's life is like a pinball machine, with him as one of the balls in a multi-ball game, there are a lot of things happening. It is a crazy life and a crazy world he is navigating as he heads into the bumpers and drop targets. But the exit gates are closed and Max keeps getting batted back up into the workings of the game.
There are many references, puns, and insights pulled from our present and past. Max's world, though different in many ways, is strongly grounded in our present. This is not a book to be looking for heavy meaning, but you might find some connection to the crazy stuff happening in your own life.
This is not a book for young readers. The themes, descriptions, and events are for the mature. This is a society where sex, drugs, and murder are everyday events. There is a constant threat of terrorism and war that is seen more as an inconvenience than a real danger. We see a world where there are few lasting consequences to the people living in it.
I recommend Birth to readers who are looking for the absurd and the outlandish.
About the Author (from the book)
S.T. Gulik is a magical cockroach.
He started life as a common wood roach in 1681, living in a small castle outside Dublin. One day, a human alchemist blew himself up while trying to brew the elixir of life. S.T. survived the blast, but he fumes cursed him with self-awareness and immortality. A lot has happened in three-hundred-thirty-five years. Everyone he knew and loved has died. Vampire movies make him cry.
On the upside, he's had countless adventures and learned many things. He worked for the goddess of chaos for one-hundred-twenty-three years. About thirty years ago, she turned him human and disappeared, which is fine because humans are smart and likable.
Oh, and he writes absurdist fiction. That's important. Gotta mention that.
I'm working at keeping my material free of subscription charges by supplementing costs by being an Amazon Associate and having advertising appear. I earn a fee when people make purchases of qualified products from Amazon when they enter the site from a link on Guild Master Gaming and when people click on an ad. If you do either, thank you.
If you have a comment, suggestion, or critique please leave a comment here or send an email to guildmastergaming@gmail.com.
I have articles being published by others and you can find most of them on Guild Master Gaming on Facebookand Twitter(@GuildMstrGmng).
Recent Painting/Basing
The Storm Is Everywhere
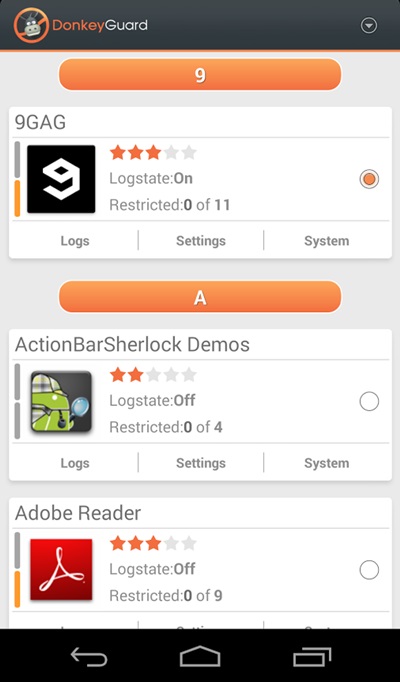
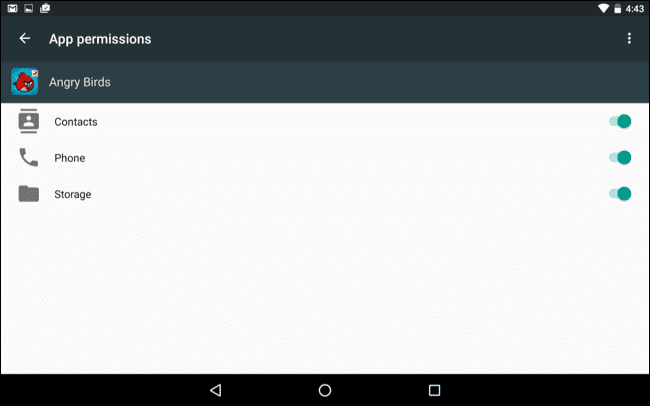
How To Protect Your Private Data From Android Apps
How To Protect Your Private Data From Android Apps
Steps To Protect Your Private Data From Android Apps:
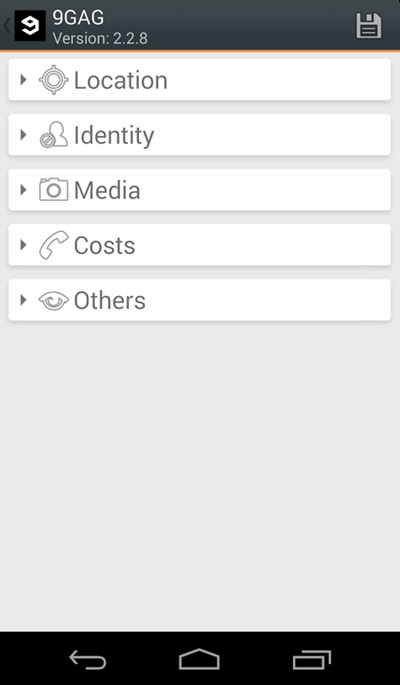
Manually Checking App Permission
Continue reading
- Hacking Tools For Kali Linux
- Hack And Tools
- Nsa Hack Tools Download
- Hacker Tools Windows
- Hackers Toolbox
- Hacker Tool Kit
- Pentest Recon Tools
- Hacking Tools Mac
- Hack Tools For Games
- Hack Tools For Mac
- Pentest Tools Alternative
- Physical Pentest Tools
- Pentest Tools For Mac
- Hacker Tools Software
- Pentest Tools For Android
- Physical Pentest Tools
- How To Install Pentest Tools In Ubuntu
- Hacker Hardware Tools
- Hacking Tools For Mac
- Hackers Toolbox
- Hacking Tools Software
- Hackers Toolbox
- Hacker Tools Free Download
- Growth Hacker Tools
- Hack Tools Mac
- Hacker Tools For Ios
- Hack Tools For Ubuntu
- Hacking Tools Windows 10
- Hacker Tools For Windows
- Top Pentest Tools
- Black Hat Hacker Tools
- Computer Hacker
- Tools For Hacker
- Hacker Tools Linux
- Hacking Tools Kit
- Hacking Tools For Games
- Hack Tools Download
- World No 1 Hacker Software
- Pentest Tools Free
- Hacking Tools 2020
- Hack Tools Online
- Hacking Tools Download
- Hacker Tools For Ios
- Pentest Tools Tcp Port Scanner
- Hacker
- Pentest Tools Subdomain
- Hacking Tools For Windows 7
- Computer Hacker
- World No 1 Hacker Software
- Pentest Reporting Tools
- Hacking Tools Mac
- Pentest Tools Framework
- Pentest Box Tools Download
- Wifi Hacker Tools For Windows
- Hack Tools
- Hacking Tools Usb
- Hackers Toolbox
- Hacker Tools For Ios
- Easy Hack Tools
- Android Hack Tools Github
- Pentest Tools Android
- Hacker Tools Online
- Hacking App
- Hacking Tools For Mac
- Hacker Hardware Tools
- Hack Tools For Mac
- Hacker Tools 2020
- Hackers Toolbox
- Hacker Search Tools
- Pentest Tools For Ubuntu
- Kik Hack Tools
- Hacker
- Top Pentest Tools
- Hacker Tools Software
- Hacker
- Pentest Tools Open Source
- Termux Hacking Tools 2019
- Hack Rom Tools
- Hack Tools Download
- Pentest Tools Framework
- Hacker Techniques Tools And Incident Handling
- Hacking Tools For Windows 7
- Hacking App
- Black Hat Hacker Tools
- Hack Tool Apk
- Pentest Tools Bluekeep
- Hacker Tools Apk
- Pentest Tools For Mac
- Computer Hacker
- Hacks And Tools
- Hacker Tools Free
- New Hack Tools
- Hacking Tools 2019
- Hacking Tools
- Github Hacking Tools
- Pentest Tools Online
- Hack Tool Apk
- Underground Hacker Sites
- Kik Hack Tools
- Nsa Hack Tools
- Pentest Tools Website
- Hacking Tools Kit
- Beginner Hacker Tools
- Hack Apps
- Hak5 Tools
- Hacker Tools Free Download
- Game Hacking
- Hacker Tools For Windows
- Hacker Search Tools
- Hacking Tools For Mac
- Pentest Tools Linux
- Hack Apps
- Hacker Tools Apk
- Pentest Tools Online
- Pentest Tools Open Source
- Hacking Tools For Windows Free Download
- Hacking Tools For Kali Linux
- Hacker Tools Mac
- Black Hat Hacker Tools
- Hack Tools 2019
- Pentest Tools Open Source
- Hack Rom Tools
- Hacker Tools Free
- Hacking Tools For Windows
- Hacking Tools Software
- Hacking App
- Free Pentest Tools For Windows
- Hacking Tools For Windows
- Pentest Automation Tools
- Pentest Tools Review
- Pentest Tools
- Easy Hack Tools
- Pentest Tools Free
- Hacker Tools Hardware
- Hacking Tools And Software
- Tools Used For Hacking
- Top Pentest Tools
- Pentest Tools For Windows
- New Hack Tools
- Hacker Hardware Tools
- Wifi Hacker Tools For Windows
- Game Hacking
Top 10 Most Popular Ethical Hacking Tools (2019 Ranking)
Top 10 powerful Hacking Tools in 2019.
If hacking is performed to identify the potential threats to a computer or network then it will be an ethical hacking.
Ethical hacking is also called penetration testing, intrusion testing, and red teaming.
Hacking is the process of gaining access to a computer system with the intention of fraud, data stealing, and privacy invasion etc., by identifying its weaknesses.
Ethical Hackers:
A person who performs the hacking activities is called a hacker.
There are six types of hackers:
- The Ethical Hacker (White hat)
- Cracker
- Grey hat
- Script kiddies
- Hacktivist
- Phreaker
A security professional who uses his/her hacking skills for defensive purposes is called an ethical hacker. To strengthen the security, ethical hackers use their skills to find vulnerabilities, document them, and suggest the ways to rectify them.
Companies that provide online services or those which are connected to the internet, must perform penetration testing by ethical hackers. Penetration testing is another name of ethical hacking. It can be performed manually or through an automation tool.
Ethical hackers work as an information security expert. They try to break the security of a computer system, network, or applications. They identify the weak points and based on that, they give advice or suggestions to strengthen the security.
Programming languages that are used for hacking include PHP, SQL, Python, Ruby, Bash, Perl, C, C++, Java, VBScript, Visual Basic, C Sharp, JavaScript, and HTML.
Few Hacking Certifications include:
Let's Explore!!
#1) Nmap

Price: Free
Description:
Nmap is a security scanner, port scanner, as well as a network exploration tool. It is an open source software and is available for free.
It supports cross-platform. It can be used for network inventory, managing service upgrade schedules, and for monitoring host & service uptime. It can work for a single host as well as large networks. It provides binary packages for Linux, Windows, and Mac OS X.
Features:
- Nmap suite has:
- Data transfer, redirection, and debugging tool(Ncat),
- Scan results comparing utility(Ndiff),
- Packet generation and response analysis tool (Nping),
- GUI and Results viewer (Nping)
- Using raw IP packets it can determine:
- The available hosts on the network.
- Their services offered by these available hosts.
- Their OS.
- Packet filters they are using.
- And many other characteristics.
Best for: Nmap is best for scanning network. It is easy to use and fast as well.
Website: Nmap
******************
#2) Netsparker

******************
#3) Acunetix

Acunetix is a fully automated ethical hacking tool that detects and reports on over 4500 web application vulnerabilities including all variants of SQL Injection and XSS.
The Acunetix crawler fully supports HTML5 and JavaScript and Single-page applications, allowing auditing of complex, authenticated applications.
It bakes in advanced Vulnerability Management features right-into its core, prioritizing risks based on data through a single, consolidated view, and integrating the scanner's results into other tools and platforms.
=> Visit Acunetix Official Website
******************
#4) Metasploit

Price: Metasploit Framework is an open source tool and it can be downloaded for free. Metasploit Pro is a commercial product. Its free trial is available for 14 days. Contact the company to know more about its pricing details.
Description:
It is the software for penetration testing. Using Metasploit Framework, you can develop and execute exploit code against a remote machine. It supports cross-platform.
Features:
- It is useful for knowing about security vulnerabilities.
- Helps in penetration testing.
- Helps in IDS signature development.
- You can create security testing tools.
Best For Building anti-forensic and evasion tools.
Website: Metasploit
#5) Aircrack-Ng

Price: Free
Description:
Aircrack-ng provides different tools for evaluating Wi-Fi network security.
All are command line tools. For Wi-Fi security, it focuses on monitoring, attacking, testing, and cracking. It supports Linux, Windows, OS X, Free BSD, NetBSD, OpenBSD, Solaris, and eComStation 2.
Features:
- Aircrack-ng can focus on Replay attacks, de-authentication, fake access points, and others.
- It supports exporting data to text files.
- It can check Wi-Fi cards and driver capabilities.
- It can crack WEP keys and for that, it makes use of FMS attack, PTW attack, and dictionary attacks.
- It can crack WPA2-PSK and for that, it makes use of dictionary attacks.
Best For: Supports any wireless network interface controller.
Website: Aircrack-Ng
#6) Wireshark

Price: Free
Description:
Wireshark is a packet analyzer and can perform deep inspection of many protocols.
It supports cross-platform. It allows you to export the output to different file formats like XML, PostScript, CSV, and Plaintext. It provides the facility to apply coloring rules to packet list so that analysis will be easier and quicker. The above image will show the capturing of packets.
Features:
- It can decompress the gzip files on the fly.
- It can decrypt many protocols like IPsec, ISAKMP, and SSL/TLS etc.
- It can perform live capture and offline analysis.
- It allows you to browse the captured network data using GUI or TTY-mode TShark utility.
Best For: Analyzing data packets.
Website: Wireshark
#7) Ettercap

Price: Free.
Description:
Ettercap supports cross-platform. Using Ettercap's API, you can create custom plugins. Even with the proxy connection, it can do sniffing of HTTP SSL secured data.
Features:
- Sniffing of live connections.
- Content filtering.
- Active and passive dissection of many protocols.
- Network and host analysis.
Best For: It allows you to create custom plugins.
Website: Ettercap
#8) Maltego

Price: The Community version, Maltego CE is available for free. Price for Maltego Classic is $999. Price for Maltego XL is $1999. These two products are for the desktop. Price for the server products like CTAS, ITDS, and Comms starts at $40000, which includes training as well.
Description:
Maltego is a tool for link analysis and data mining. It supports Windows, Linux, and Mac OS.
For the discovery of data from open sources and visualizing the information in graphical format, it provides the library of transforms. It performs real-time data-mining and information gathering.
Features:
- Represents the data on node-based graph patterns.
- Maltego XL can work with large graphs.
- It will provide you the graphical picture, thereby telling you about the weak points and abnormalities of the network.
Best For: It can work with very large graphs.
Website: Maltego
#9) Nikto

Price: Free
Description:
Nikto is an open source tool for scanning the web server.
It scans the web server for dangerous files, outdated versions, and particular version related problems. It saves the report in a text file, XML, HTML, NBE, and CSV file formats. Nikto can be used on the system which supports basic Perl installation. It can be used on Windows, Mac, Linux, and UNIX systems.
Features:
- It can check web servers for over 6700 potentially dangerous files.
- It has full HTTP proxy support.
- Using Headers, favicons, and files, it can identify the installed software.
- It can scan the server for outdated server components.
Best For: As a Penetration Testing tool.
Website: Nikto
#10) Burp Suite

Price: It has three pricing plans. Community edition can be downloaded for free. Pricing for Enterprise edition starts at $3999 per year. Price of the Professional edition starts at $399 per user per year.
Description:
Burp Suite has a web vulnerability scanner and has advanced and essential manual tools.
It provides many features for web application security. It has three editions, community, enterprise, and professional. With community editions, it provides essential manual tools. With the paid versions it provides more features like Web vulnerabilities scanner.
Features:
- It allows you to schedule and repeats the scan.
- It scans for 100 generic vulnerabilities.
- It uses out-of-band techniques (OAST).
- It provides detailed custom advisory for the reported vulnerabilities.
- It provides CI Integration.
Best For: Security testing.
Website: Burp Suite
#11) John The Ripper

Price: Free
Description:
John the Ripper is a tool for password cracking. It can be used on Windows, DOS, and Open VMS. It is an open source tool. It is created for detecting weak UNIX passwords.
Features:
- John the Ripper can be used to test various encrypted passwords.
- It performs dictionary attacks.
- It provides various password crackers in one package.
- It provides a customizable cracker.
Best For: It is fast in password cracking.
Website: John the Ripper
#12) Angry IP Scanner

Price: Free
Description:
Angry IP Scanner is a tool for scanning the IP addresses and ports. It can scan both on local network and Internet. It supports Windows, Mac, and Linux operating systems.
Features:
- It can export the result in many formats.
- It is a command-line interface tool.
- It is extensible with many data fetchers.
Website: Angry IP Scanner
Conclusion
As explained here, Nmap is used for computer security and network management. It is good for scanning the network. Metasploit is also for security and is good for building anti-forensic and evasion tools.
Aircrack-Ng is a free packet sniffer & injector and supports cross-platform. Wireshark is a packet analyzer and is good in analyzing data packets. As per the reviews available online, people recommend using Nmap instead of Angry IP scanner as Angry IP Scanner comes with unwanted applications.
John the Ripper is fast in password cracking. Nikto is a good open source tool for penetration testing. Maltego presents the data in a graphical form and will give you information about weak points and abnormalities.
This was all about the ethical hacking and the top ethical hacking tools. Hope you will find this article to be much useful!!
@EVERYTHING NT
Related news
- Hack Tools Mac
- Hack Tools Online
- Hacking Tools Download
- Pentest Tools Windows
- Hacking Tools
- Hacking Tools 2020
- Pentest Tools Find Subdomains
- New Hack Tools
- Hack Tools
- Physical Pentest Tools
- Bluetooth Hacking Tools Kali
- Blackhat Hacker Tools
- Pentest Tools Framework
- Easy Hack Tools
- Wifi Hacker Tools For Windows
- Hack App
- Hacker Tools Mac
- Pentest Box Tools Download
- Hacker Tools For Ios
- Hack Tools Mac
- Hack And Tools
- World No 1 Hacker Software
- Pentest Tools Find Subdomains
- Android Hack Tools Github
- Hacker Tools Apk
- Hack Tools For Mac
- Hacker Tools 2020
- Hackers Toolbox
- Hacking Tools Kit
- New Hack Tools
- Pentest Tools Online
- Pentest Tools Linux
- Hacking Tools For Games
- Hack Tools For Windows
- Pentest Tools Windows
- Hacking Tools Github
- Pentest Tools Bluekeep
- Pentest Tools
- Pentest Tools Subdomain
- Pentest Tools Github
- Growth Hacker Tools
- Top Pentest Tools
- Pentest Tools Download
- Pentest Tools Alternative
- Pentest Tools Url Fuzzer
- Hacking Tools Pc
- Nsa Hacker Tools
- Pentest Tools Bluekeep
- Hack Tools
- Hacking Tools
- Hacking Tools And Software
- Hacker Tools Linux
- Pentest Tools Find Subdomains
- Hacker Tools Online
- Free Pentest Tools For Windows
- Hacking Tools Software
- Hacking Tools Name
- Kik Hack Tools
- Best Pentesting Tools 2018
- Hack Tools Download
- Hacking Tools Mac
- Hacking Tools Windows 10